One of my grandfathers worked for a telephone company before he passed. That man was an absolute pack rat, he wouldn’t throw anything away. So naturally he had boxes and boxes of punch cards in this basement. I guess they were being thrown out when his employer upgraded to machines that didn’t need punch cards, so he snagged those to use as note paper. I will say, they were great for taking notes. Nice sturdy card stock, and the perfect dimensions for making a shopping list or the like.
- 0 Posts
- 97 Comments

 3·1 month ago
3·1 month agoI haven’t actually tried the new ones, I probably should do that before I slander them. The Harvest Cheddar ones were so good though. I haven’t seen them in at least a few years, unfortunately.

 5·1 month ago
5·1 month agoI noticed that Miss Vickie’s has a new sour cream something or other flavour in a bag that’s the same colour, or nearly so. Every time I go through the chip aisle I get very excited for a second, then I realize it’s not actually the Harvest Cheddar and my hopes are dashed. I’m developing an irrational hatred of those impostor chips.

 33·2 months ago
33·2 months agoThe plow. It allowed early river valley peoples to generate semi-reliable food surpluses, and those food surpluses triggered everything that came after. I can’t take credit for this argument, I first encountered it in this episode from the first season of Connections.

 44·2 months ago
44·2 months agoThere is a Unicode Technical Standard for this, called the Unicode Collation Algorithm. Whether everyone uses it, I can’t say. As it says on the linked page:
Conformance to the Unicode Standard does not imply conformance to any UTS.
So in other words it’s possible to conform to the Unicode Standard without adhering to the Unicode Collation Algorithm.
whatever this is: ¦
That is the pipe symbol, or vertical bar. When it has a gap in the middle it may be known as the broken pipe symbol or broken bar. It’s considered the same symbol with or without the gap. Early terminals displayed it with a gap to make it distinguishable from lower-case L characters.

 15·3 months ago
15·3 months agoNot sure if any of these are close to you, but several libraries in western Canada seem to have copies available to borrow:
- Vancouver Public Library
- Prince Albert Public Library (Saskatchewan)
- Parkland Regional Library (Saskatchewan)
If you’re not close to any of those libraries, try asking at your local library. They may have some means of doing an interlibrary loan, or have other suggestions.

 474·3 months ago
474·3 months agoHardly the first time. I’d argue the US made the same mistake in Afghanistan in 2003, diverting resources to Iraq because Bush Jr. had such a hard-on for Saddam.

 7·3 months ago
7·3 months agoGuy Gavriel Kay. First book published in 1984, part of a trilogy that was Tolkien-esque, quite decent, but not exactly ground-breaking. He’s since gone on to something a little more unique, which he describes as “historical fiction with a quarter-turn to the fantastic.” Impeccably researched but set an alternate world that’s a close but not exact mirror of our own. This allows him to take a few small liberties with historical accuracy in service of telling a better story. Personally I think he really hit his stride in 1995 with The Lions of Al-Rassan, and almost everything he’s written since then has been exceptional.

 42·4 months ago
42·4 months agoSumming a balance column is never correct. Take any example that doesn’t end in a zero balance and it’s easy to see that the balance column’s sum is meaningless:

I’m sure there would be a way to do this with Debian, but I have to confess I don’t know it. I have successfully done this in the past with Clover Bootloader. You have to enable an NVMe driver, but once that’s done you should see an option to boot from your NVMe device. After you’ve booted from it once, Clover should remember and boot from that device automatically going forward. I used this method for years in a home theatre PC with an old motherboard and an NVMe drive on a PCIe adapter.

 16·4 months ago
16·4 months agoThe game had an 8-hour free trial. That would drive the “engagement” they’re talking about, and I’m guessing it’s the only positive news they have. If the game was selling well or had significant daily active users, they’d be talking about that instead.

 141·4 months ago
141·4 months agoDepends on the color of the wall, but likely no. A matte black wall would absorb a lot of light, a matte white wall would reflect most of the light. Other colours would fall somewhere in the middle, reflecting some wavelengths and absorbing others. The only difference with a mirror is that it reflects light in a uniform fashion, whereas a painted wall will generally scatter reflected light. But scattered light still contributes to total light output! The only scenario where a mirror behind a lamp would come close to doubling light output would be if the wall we’re comparing against is painted with Vantablack or some other ultrablack paint that absorbs 99%+ of the light from the lamp.

 41·4 months ago
41·4 months agoYeah, that’s definitely a thing. They need to implement an idle timer. Seems like a low effort feature that would improve the login experience significantly.

 17·4 months ago
17·4 months agoSame playbook the IDF ran during the Sabra and Shatila massacre. Cordon off an area and let some militia do the dirty work. Bet they’ll investigate themselves after the fact and conclude they had no “direct responsibility”, just like they did previously.

 10·4 months ago
10·4 months agoIf you look at the Steam player charts for the game you’ll see when it’s working vs. when it’s not. Off-peak it works fine, but right now the player base is ramming up against their temporary player cap for hours at a time on-peak. If you try to connect when there are thousands of others also trying to connect, that’s when things go south. That was the case for much of the weekend.
Edit: Here’s a chart illustrating what I mean:
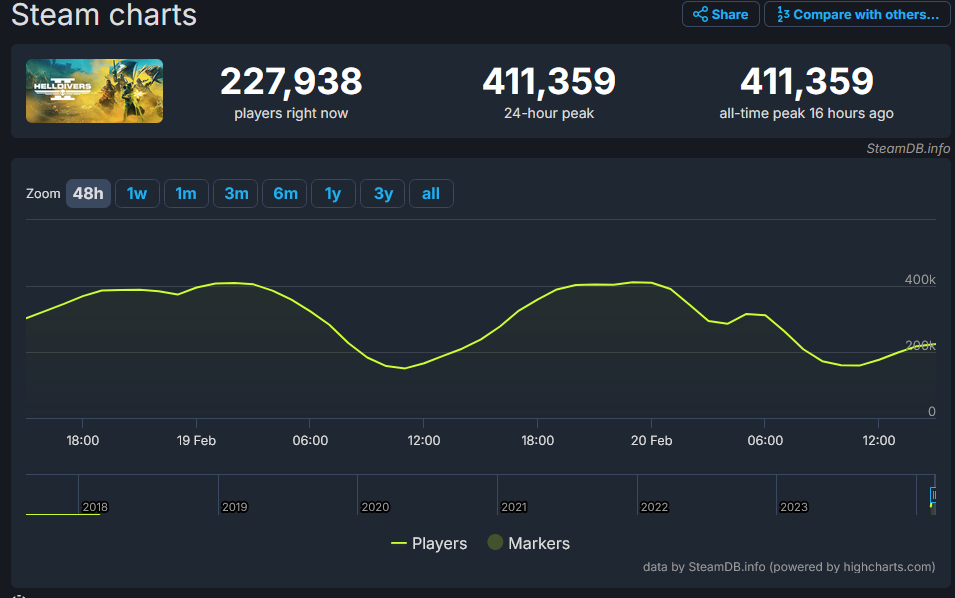
In the last 48 hours, player counts hit 400k at about 7pm
EasternUTC and just stayed there for 6-ish hours. That isn’t normal, almost all other player count charts show a gradual rise and fall over the course of a day. The devs implemented an artificial cap after they found that their servers bog down when there are too many active players, basically sacrificing the peak time login experience to preserve the in-game experience. If you try to connect while the active player count is pegged, you’re essentially joining a swarm of other players who are also trying to connect at the same time. That swarm is likely DOSing some aspect of their own login systems.

 6·4 months ago
6·4 months agoIf you let it sit on the black screen, it will eventually let you in. Or to be exact it will eventually display the intro movie and splash screen, you’ll probably see servers at capacity there and after some time there you’ll eventually get in. Not exactly sure what it’s doing on that black screen, but I’m guessing it’s trying to talk to some server that’s massively overloaded. I spent most of the weekend playing with friends, so I had to suffer through the wait multiple times.

 5·5 months ago
5·5 months agoWhen I fly to the US from Toronto I clear US customs in Pearson Airport, before getting on the plane. If I were to sign up for a Nexus pass I’d be able to pass through US customs even faster, but I don’t travel often enough for it to be worthwhile. Not sure if either of those matches what you mean by pre-clearance.

 14·5 months ago
14·5 months agoThere are some viruses that have targeted Linux, but they’re rare compared to other platforms and their ability to spread is relatively low. One of the main reasons is just down to how software tends to be installed on each platform. Viruses have an easier time spreading on Windows or OSX where users are more accustomed to downloading an executable and running it. Once there’s a malicious running process, it has a comparatively high chance to spread because it can attempt to escalate its privileges either by exploiting a bug or socially engineering the user to click through a privilege escalation prompt. That entire workflow is practically nonexistent on Linux, users just don’t tend to download and execute random binaries. Instead most Linux software gets delivered in one of these ways, each of which has impediments that reduce the chance a virus could spread:
- through an OS repo; it would be difficult for a malicious actor to get a virus through the release process and into a trusted repo
- through a public source like Github; again it would be difficult for a malicious actor to get a virus into public source code without someone noticing
- through a container image from an image library like DockerHub; I believe a malicious container would be sandboxed, making it hard if not impossible for that container to take over the host system
- through an application image like a snap, flatpak or appimage; again, I believe these run in their own sandbox from which they would have difficulty breaking out
There are some exceptions, for example some companies like Hashicorp will distribute their stuff as precompiled binaries. Even in that case you’re probably fine as long as you don’t run the downloaded binary as root. Users in the habit of downloading strange binaries from sketchy places and running them as root just aren’t very common among the Linux userbase. I’m sure there are some (and they should really stop doing that), but there aren’t enough of them to allow a virus to spread unchecked.

 451·5 months ago
451·5 months agoI don’t think dedicated antivirus software is really required anymore. I haven’t run third-party AV software on any of my systems in the last decade.
On Windows, the built-in Windows Defender is good enough for most use cases. When it first launched Defender had a pretty bad track record at stopping viruses, but now it routinely ranks at the top.
On Linux, antivirus software has never really been required. One major exception I can think of would be if you’re running a file server or mail server that talks to OSX or Windows systems. Even then the AV software isn’t really there to protect the server, it’s there to make sure you don’t pass malware or viruses to those non-Linux clients.



Because the toxins your body is reacting to are already in your bloodstream. It’ll take time for those to get metabolized by your liver, and how much or little you vomit won’t change how much work your liver has to do.